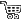|
Last updated on Tuesday 16th of November 2021 08:30:50 PM XSIBackup-Pro GUI Manual 1/7Cron Management Please note that this post is relative to old deprecated software ©XSIBackup-Classic. Some facts herein contained may still be applicable to more recent versions though. Please note that this post is relative to old deprecated software ©XSIBackup-Classic. Some facts herein contained may still be applicable to more recent versions though.
For new instalations please use new ©XSIBackup which is far more advanced than ©XSIBackup-Classic. The "Cron" menu entry is quite simple to operate with. It only has too options: install and uninstall. 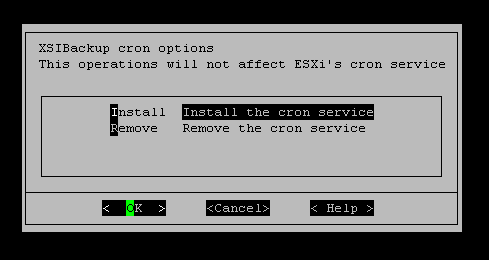
By installing the crontab you will be adding an entry to the /etc/rc.local.d/local.sh file, so that every time you reboot the server, a copy of the crontabs corresponding to every user with an associated cron schedule will be re-introduced to the corresponding ESXi crontab. This is necessary as ESXi's crontabs are not persistent. When installing and uninstalling the crontabs, you will be presented a list of users to choose from. Those are users of the ESXi host. So you need to add a user to your system before being able to install his crontab. You will also need to assign appropriate privileges, so that the user has enough permissions to perform the backups. This is equivalent to creating a user and assigning full permissions. It is highly recommended that, unless you are ready to go through the backup user creation and permissions asigment, you stick to using root as the backup user. 
Key Exchange Please note that this post is relative to old deprecated software ©XSIBackup-Classic. Some facts herein contained may still be applicable to more recent versions though. Please note that this post is relative to old deprecated software ©XSIBackup-Classic. Some facts herein contained may still be applicable to more recent versions though.
For new instalations please use new ©XSIBackup which is far more advanced than ©XSIBackup-Classic. Linking to another host means adding the current host's public key to the authorized_keys file in the second host. This allows to login from host A to B without being prompted for a password. You need to Link to other hosts before you can execute any crossed backup jobs by means of the --host argument, or when you simply want to backup to it via IP instead of to a local datastore. 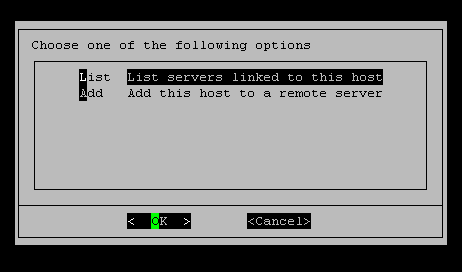
XSIBackup Menu offers two options in regards to linked hosts: - List servers linked to the current host, which presents a list of public keys present in the local server's authorized_keys file. This shows which ESXi servers (they could also be other kind of OSs) are allowed to SSH into this server by using an RSA key. XSIBackup uses its own key pair, which has nothing to do with the host's key pair, which BTW is not persistent in ESXI (as so many other things). So it's XSIBackup's public RSA key that is added to the remote server's authorized_keys file. XSIBackup is able to use this menu option to detect SSH folders and add keys on *NIX servers based on systemd and init.d service managers, but it will not work out of the box with any OS you can think of. So, in case you get some error and you can't use the menu, just grab the xsibackup_id_rsa.pub key and add it to the remote server's authorized_keys file. |


|
Login • Available in: