|
Last updated on Monday 15th of May 2023 12:02:09 PM Protect ©VMWare ©ESXi VMs from ransomwareTake precautions and use the right tools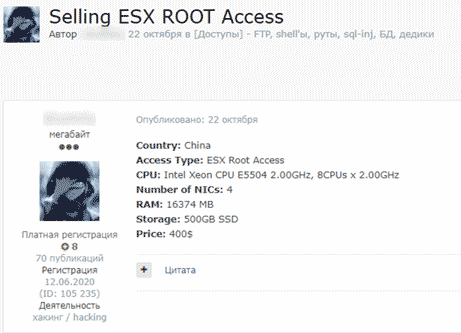
 Winter 2023: there has been a massive ransomware attack on ©ESXi servers,
read here on how to protect your ©ESXi hosts
Winter 2023: there has been a massive ransomware attack on ©ESXi servers,
read here on how to protect your ©ESXi hosts
PrefaceDo not panic. ©ESXi is a good OS, it's well protected and just a bit of time and dedication from your part will make it very difficult that ransomware affects your hosts.Ransomware attacks are generally random, thus getting "out of the way" will generally be enough. What do we mean by that?: well, just do not follow predictable patterns. Ransomware hackers put their scripts to work on ranges of IPs where they believe some given OS to exist. In this case ©ESXi. Then they try a brute force attack on well-known ports or try to exploit some known vulnerability. This attack can be on SSH port 22 or any of the services exposed to the internet, like the HTTP GUI. Unless they are going for you, and this is a very rare "honour" (unless you do have some valuable information that somebody wants to steal), getting out of the fire line will save you 99% of the trouble. What does getting out of the fire line mean?: don't use well-known ports, use long passwords and filter out traffic with a firewall. ©ESXi's firewall is a toy. We won't enter into why it happens to be like that but just how to work this problem around. If you are hosting your ©ESXi servers on premises, you have control on your network design, just hide your servers behind a firewall, redirect traffic on non-standard ports from the outer part of your router and filter traffic based on their source. On top of that use long passwords and remove any access to unnecessary services. If you are not going to use the Windows client or the GUI from the outside world, just avoid any NAT mappings to them or even disable access to them if they aren't going to be used. Nevertheless, you will still need a way to recover your data. Not just to protect from a successful ransomware attack (which will be an extremely unlikely event if you follow the above advice), but to recover your Virtual Machines or files as needed or as just part of your enterprise's Disaster Recovery Protocol. Our ©VMWare ©ESXi backup software will allow you to replicate and/or backup your VMs to any local datastore or remote filesystem over IP. This allows to easily create a hot site with a vast amount of recovery points thanks to deduplication. That will guarantee Business continuity in case of a mayor software or hardware problem. As you can see, protecting against Ransomware is in open relationship with protecting against any other threat and can be easily addressed with the tools we offer and some common sense. The matterRansomware malware is growing rapidly and destroying the enterprise data at the cost of a ransom to be able to decrypt it. Specialized journalists claim that this is one of the biggest illegal activities nowadays by income grow.Every day the news tell about some new big enterprise or government affected by this disease. Nobody recognized to pay the extortion, nonetheless, unofficially the leaked news tell about a different story. Ransomware consists in encrypting the data of an institution, enterprise or individual by employing a malware binary. The way it gets into your enterprise is generally through the e-mail inbox, disguising itself as some parcel service delivery note, some zipped document from your bank, or some order from a client. Some years ago they were poorly designed and the encryption could even be reversed by employing advanced forensic tools. Nowadays things have changed and they employ deep encryption keys, making it impossible to revert it. Thus, you'd better make sure that you are prepared, in the event that somebody in your office bites the bait. Can you imagine what could be for your enterprise to loose all of its data?, are you sure you have a recent backup ready to be restored rapidly? Until very recently ransomware was designed to be executed on Windows platforms, but criminals know very well that nowadays the number of desktops that have been virtualized is very high. They are starting to target virtualization platforms like ©ESXi. Recently, ransomware for ©ESXi, exploting some of the vulnerabilities of this Hypervisor OS has been detected. This new form of malware will try to encrypt your virtual disks. If you backup to some local datastore, your chances that your backup copies are encrypted too are high. Our ©VMWare ©ESXi backup software allows to backup over IP/SSH adding an extra layer of protection, as malware is executed locally. There are different ways to minimize the possibility of a successful ransomware attack in different platforms, let's revise them: NetworkingUse NAT preferably over bridged configurations. There are many different ways in which you can implement this. From the most classical one, by using some networking hardware and splitting your networks in subnets, to logical ones by using the networking capabilities of ©VMWare ©ESXi.The latter will save you time and money, as you will not need any additional physical devices, but will on the other hand be as effective as a classical approach. We have prepared this totally free OpenWRT based firewall device that comes preconfigured as a NAT router to divide your ©ESXi host's network into an outer and a NATed inner subnet with port forwarding and filtering. Use a good and recent antivirus softwareYou should be specially concerned if you are a ©MS Windows desktop user. Guess what, cybercriminals work on statistical possibilities. Most viruses and malware is designed for Windows desktops.Linux and Mac OS users are more safe, still, the chances that you are affected by some ransomware episode is also high, in this case due to the probably excesive confidence you have in being safe. And overall, please do make sure that your AV software is updating itself. Design your systems to be resilient to infectionsDevise systems that difficult an eventual infection from propagating through your network shares. Forcing users to enter their password on network shares might make you even more unpopular than you are now, still it's for the common good.Keep your databases: ERP, CRM, Accounting, etc... in isolated servers not sharing any folder with destop users. I know this is not easy in an SME with reduced budget, still ©ESXi is still free to use as a basic hypervisor. You have other mature platforms out there. Take the time to learn and use a virtualization platform for your servers, so that you can isolate them in a more convenient way. And of course back them up every day and make sure that the copies are in a safe place. Ransomware affecting virtualization platformsMalware affecting other type of more specialized OSs, like virtualization hypervisors, is still rare, it will grow rapidly, you can bet it. Try to think ahead, devise strategies to keep your data protected, like backing up over IP. Reduce permissions on the folders where you have your SSL keys to the bare minimum, like 0400. This will allow your backup software to use them to athenticate against remote servers, but will reduce the chances some malware encrypts them.Grab your keys from a remote SSH server by using another key. I know this sounds a bit crazy, it's easy to implement and no ransomware programmer will try to target eccentric geeks, remember they depend on the Gaussian distribution to make money. We will cover this technique in a different post. Well, as you can see, there are a number of ways to increase your level of protection against the bad guys. The most fundamental one: don't do the same as the rest. Users will sooner or later click on some ransomware binary, it's just a matter of time. Rare is the day I don't receive 10 to 20 e-mails with such content. My AV is not able to detect them all, maybe just two thirds, and I use one of the best. |


|
Login • Available in: