|
Last updated on Monday 28th of February 2022 08:52:48 PM ©ESXi Firewall WorkaroundHow to overcome the limitations of the ©ESXi FirewallThe ©ESXi Firewall was never very customizable. It included some predefined rules that you could turn on and off and for those of us a little bit more exigent with this feature, we could always edit the firewall .xml configuration file to add our custom rules.The need for a functional firewall in ©ESXi is dependent on your setup. If you use NAT you can always use some firewall virtual machine to filter traffic to some virtual LAN inside your ©ESXi host. Still, the ©ESXi FW will affect the traffic coming in and out of the very ©ESXi OS, which is something of special interest to those of you using ©XSIBackup, as it works as an ©ESXi service. 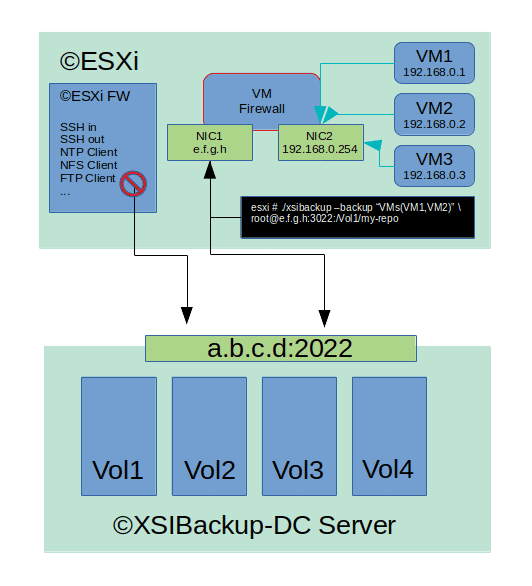
The thing is that in latest versions of ©ESXi, the possibility to add your custom rules has been waived. This forces users to use the predefined SSH-out rule to copy VMs out of the ©ESXi box. This is OK to be done in a LAN with perimetral security, still using default SSH port 22 in a server with an Internet IP is becoming a risk sport in the last years. You can always limit access by IP, nonetheless this is not always possible and working with a toy firewall can become frustrating. Luckily the ©ESXi shell can directly communicate with any briged NIC belonging to any of your VMs and your VMs are not limited by the ESXi firewall. This makes it feasible and extremely convenient to use some FW VM listening with an interface briged to your ©ESXi NIC to act as the firewall of your ©ESXi shell. Per instance, let's say that you would like to reach some non standard port, like 2022 in some internet server that is serving as your ©XSIBackup-DC backup server. You won't be able to do so directly, as the ©ESXi firewall doesn't have any predefined outwards rule for port 2022. Still you can very well reach any IP in any VM, per instance e.f.g.h in our example. To be able to do so you will need some iptables firewall. We won't enter into any details by now, any iptables firewall in some Linux device with kernel 2.6.32 or above will do it. This corresponds to some CentOS/RHEL 6.7 or above release. You could also use some newer release of this family of Linux distros: RHEL/CentOS/Rocky/Fedora, etc..., but using some older release you will be able to install to some tiny virtual hard disk and boot it up with fewer resources. (*) Some FreeBSD 7 or 8 would also be a perfect match and you would be able to run it with as little as 64 MB of RAM with a pretty heavy load. Our example consists in an ©ESXi box with an internet IP and a firewall VM with two legs. The outer leg is bridged to the ©ESXi IP, thus you can reach it from within the shell. The other leg is sitting in a virtual LAN with the address 192.168.0.0/24 The concept is easy, many of you may already be using something similar. The key feature here is something which is a bit awkward, still just a bit. Instead of creating a NAT rule via the NAT table and PREPROCESSOR rule of IP tables between the outer interface and the inner one to redirect traffic to some VM sitting in the LAN segment, we will just perform a TCP redirect to some server out in the internet. Iptables allows to do so, still most firewall appliances built on top of it like PFSense or OpenWRT will hide this possibility and only allow to perform NAT mapping between the available interfaces in the router. Thus, using a raw iptables install in some old Linux version is a nice way to remove that limitation. Once your iptables firewall is setup and running, you just need to add some rule like the one below in the *nat table of the /etc/sysconfig/iptables configuration file, in some custom script or add it manually, like in the example below, in which we set the outer leg of the router appliance to listen at port 3022 and redirect that traffic to port 2022 at the internet address a.b.c.d
iptables -t nat -A PREROUTING -s [ESXi IP] -i eth0 -p tcp -m tcp --dport 3022 -j DNAT --to-destination a.b.c.d:2022
(*) Note that you will generally want to limit access to just the IP of the ©ESXi box, so that port 3022 is not reachable from the Internet. To build a linux firewall you will need to add two NICs to it and to enable IPv4 forwarding, this will allow to foward IP packets between the NICs in your firewall and also to some outer IPs like described in this post. Usefull links: 1/ A beginners guide to IPTables 2/ In depth guide to IPTables 3/ Enable IPv4 forwarding |


|
Login • Available in: